Penetration Testing Services
Acting like ruthless hackers, HIFENCE
professionals expose system weaknesses and
provide solutions to fix them.
The best defense against sophisticated security attacks is to take the offense by testing your
own defenses, and shoring up the weaknesses.
Another day, another costly ransomware attack is in the news. And there are far more that you don’t hear about.
All of which should make you ask, “Are we next?”
To be sure that you’re not, HIFENCE Penetration Testing professionals assume the roles of the most sophisticated hackers out there, trying every way possible to find your system’s weaknesses, exploit them, and enter your environment. That’s when we put our white hats back on to help you shore up any weaknesses we found.










Key Features:
-
Custom-Tailored to Your Unique Business
Custom-Tailored to Your Unique Business
Your penetration test starts after the HIFENCE Architects Team first matches your security objectives and roadmaps with your business objectives, all to transform cybersecurity into an invaluable business enabler. -
Comprehensive Penetration Test Delivers Realistic Findings
We test your networks, servers, applications and APIs for security vulnerabilities. If vulnerabilities are identified, we go to work exploiting them. We then make realistic recommendations based on our findings and advise how you can further improve your security posture.
-
Reduces Errors and Downtime and Identifies and Remediates Device Vulnerabilities
On a monthly basis, you will receive a trend analysis from HIFENCE. It will show what improvements can be made to your network to reduce any downtime that might appear from errors or vulnerabilities.
-
Meet Your Compliance Requirements
All of the most important standards are addressed, including PCI-DSS, ISO 27001, HIPAA, SOX, and others.
-
Prioritize Your Security Budget
As an added benefit, penetration testing report will help you prioritize your security budget and show you where the next investments should be made.
-
Avoid Financial Loss
The damages a single breach of your systems can cause easily reach into the millions of dollars. But HIFENCE Penetration Testing can protect your organization from such catastrophic damages.
Simulated Attacks on Systems and Network Infrastructure to Detect and Exploit Vulnerabilities
One of the most appreciated services we provide to our clients is to ruthlessly attack their infrastructure with everything we’ve got. In the ever-evolving world of cyberattacks, our Penetration Testing experts are as relentless and sophisticated as today’s most dangerous cybercriminals — which is precisely what our clients want and need from us. By finding and exploiting a system’s weaknesses, we can then secure and remedy them before the bad actors arrive.
HIFENCE Penetration Testing, along with our Vulnerability Management Services, deliver the double layer of security for the highest level of protection. Considering that the average cost of a data breach is around $4 million, it’s clear why clients regard our Penetration Testing as such a valuable service.
HIFENCE Managed Network Services Covers:
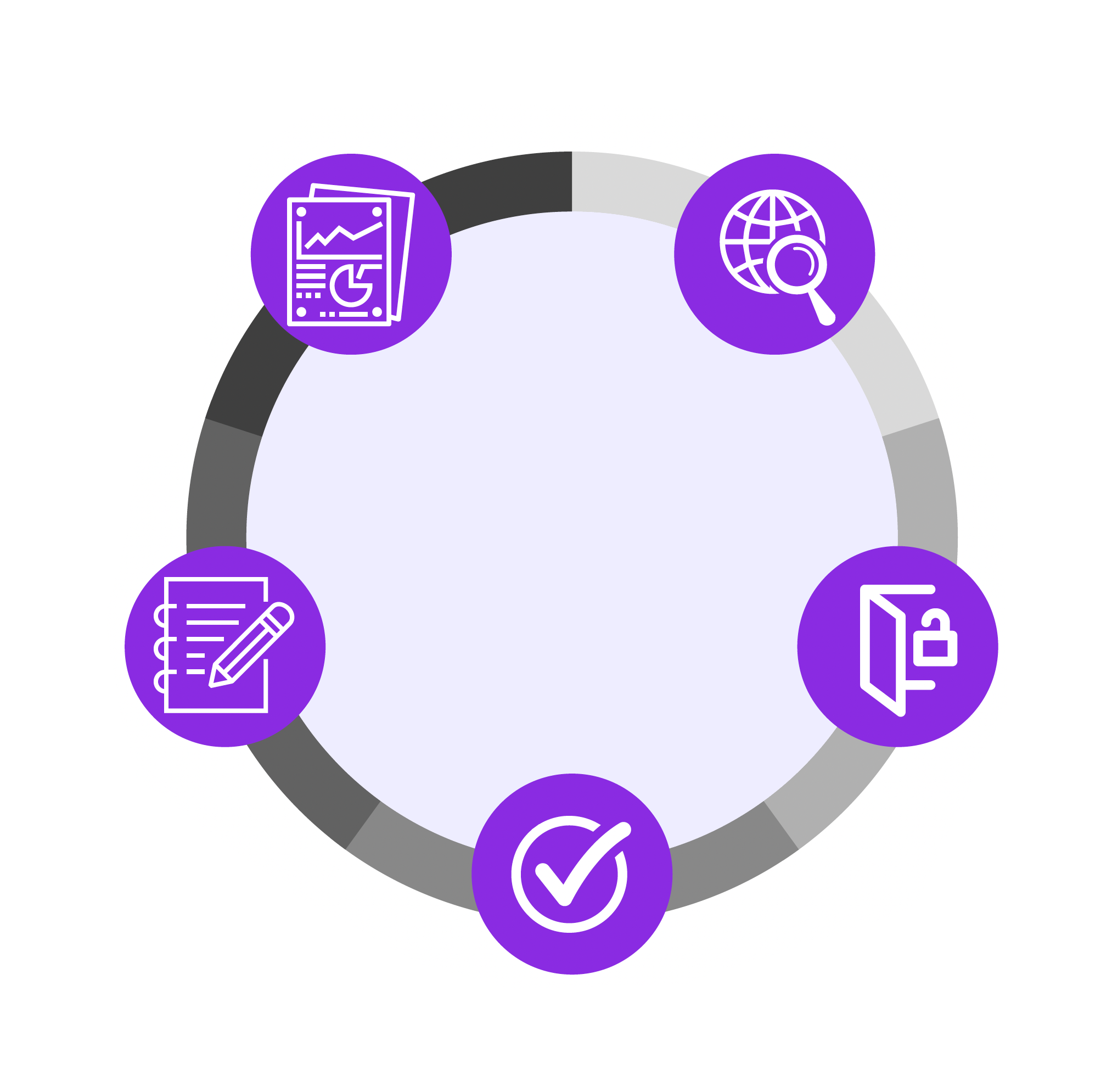
01. PLANNING &
RECONNAISSANCE
We define together the scope andobjectives of the pentest, we
gather information about the
target system or network, and
identify potential vulnerabilities.
05. ANALYSIS &
REPORTING
This involves documenting
the findings of the pentest
and presenting them to
the relevant parties.
Penetration
testing
03. GAINING ACCESS
We establish a foothold on
the target system or network
and maintain access to it over
time.
02. SCANNING
We scan the target system
or network to identify open
ports, services, and potential
vulnerabilities.
03. GAINING ACCESS
We exploit identified
vulnerabilities to gain
access to the target
system or network.

01. PLANNING RECONNAISSANCE
identify potential vulnerabilities.

02. SCANNING

03. GAINING ACCESS

04. MAINTAIN ACCESS

05. ANALYSIS & REPORTING

Today’s Security Challenges
The cost of an average data breach rose from $3.86 million to $4.24 million, with lost business representing the largest share of these costs, at $1.59M [1].
HIFENCE Penetration Test services keep your entire company safe and secure by providing a comprehensive test of your environment. We act like ruthless hackers to expose system weaknesses, and then we provide the right solutions to fix them.
Having the wrong security solution.
By using our pentest you can also see the way your security
solution reacts to threats. Are they as good as they are
advertised? Are they configured correctly or do they simply
leave the attack pass?
It takes an average of 287 days — that’s over 9 months — to detect and contain a breach, with 212 days needed just to identify a breach, and 75 days to contain it [2].
While performing our penetration tests you can also test your
internal security team to see if they can identify, alert and stop
the actions performed by our security pentester professionals.
Most companies are reactive to cyber threats, paying attention to cybersecurity only after they are breached — and that’s far too late.
But by performing the security pentest, you can make sure
that you are proactive and identify the cyber threats before
any bad actor has a chance to take advantage of it.
How Does HIFENCE Penetration Testing Help?
With decades of experience, HIFENCE security experts provide advanced pentesting services that will expose your infrastructure weaknesses. We then make recommendations on how you can fix them to further improve your security posture.
Types of Penetration Testing
OBJECTIVES
BENEFITS
External Penetration Testing
Internet by your systems, applications and services.
Internal Penetration Testing
HIFENCE performs both authenticated and unauthenticated scans so you can have a more thorough view on your vulnerability landscape.
Wireless Penetration Testing
Web Application/API Penetration Testing
Assesses web applications or API for vulnerability that can go towards system compromise or data exposure.
Cloud Penetration Testing (AWS/Azure)
Social Engineering
OSINT Testing
Custom Apps
We help you with pentest for custom or off-the-shelve applications like: Magento, WooCommerce, OpenCart, PrestaShop, Drupal, Laravel, Symfony, Yii 2.0, WordPress, API, Web App, Joomla and Online Shops
An overview of the vulnerabilities of your custom or off-the-shelve applications
Know It All:
Get the Penetration Testing Datasheet
You’ll learn, in clearly explained detail, how the features and benefits of our Penetration Testing services will help your company be safer and more secure, so you can focus on its success.

What makes us
different
You’ll like this: We’re not like other Cybersecurity providers.
We didn’t set out to have a different way of delivering the best Cybersecurity and Networking services you can have. But we — and our clients — are glad we do.
The difference is simplicity.
You’ll like this: We’re not like other Cybersecurity providers.
We didn’t set out to have a different way of delivering the best Cybersecurity and Networking services you can have. But we — and our clients — are glad we do.
The difference is tossing out
the cookie cutter.
The difference is all that we do is protect all that you do.
The difference is we’ll provide everything you need, and not
one thing you don’t.
Schedule Your
Free Consultation
A HIFENCE expert will conduct a quick overview of your current cybersecurity and networking infrastructure and discuss roadmaps for achieving your desired level of protection, based on your business objectives.
